A Trojan horse, or Trojan, is a hacking program that is a non-self-replicating type of malware which gains privileged access to the operating system while appearing to perform a desirable function but instead drops a malicious payload, often including a backdoor allowing unauthorized access to the target's computer. These backdoors tend to be invisible to average users, but may cause the computer to run slowly. Trojans do not attempt to inject themselves into other files like a computer virus. Trojan horses may steal information, or harm their host computer systems. Trojans may use drive-by downloads or install via online games or internet-driven applications in order to reach target computers. The term is derived from the Trojan Horse story in Greek mythology because Trojan horses employ a form of “social engineering,” presenting themselves as harmless, useful gifts, in order to persuade victims to install them on their computers.
Purpose and uses
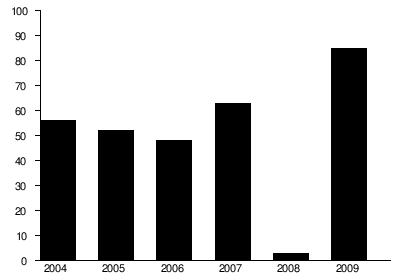 |
| This chart shows the percentage of malware that represent the trojans |
A Trojan may give a hacker remote access to a targeted computer system. Operations that could be performed by a hacker on a targeted computer system may include:
- Use of the machine as part of a botnet (e.g. to perform automated spamming or to distribute Denial-of-service attacks)
- Crashing the computer
- Blue screen of death
- Electronic money theft
- Data theft (e.g. retrieving passwords or credit card information)
- Installation of software, including third-party malware and ransomware
- Downloading or uploading of files on the user's computer
- Modification or deletion of files
- Keystroke logging
- Watching the user's screen
- Viewing the user's webcam
- Controlling the computer system remotely
- Reformatting disk
- Encrypting files
- Data corruption
- Modifications of registry
- Overheating CPU and GPU.
- Using computer resources for coin mining.
- Linking computer to Botnet
- Using infected computer as proxy for illegal activities and attacks on other computers.
Trojan horses in this way may require interaction with a hacker to fulfill their purpose, though the hacker does not have to be the individual responsible for distributing the Trojan horse. It is possible for individual hackers to scan computers on a network using a port scanner in the hope of finding one with a malicious Trojan horse installed, which the hacker can then use to control the target computer.
A recent innovation in Trojan horse code takes advantage of a security flaw in older versions of Internet Explorer and Google Chrome to use the host computer as an anonymizer proxy to effectively hide internet usage. A hacker is able to view internet sites while the tracking cookies, internet history, and any IP logging are maintained on the host computer. The host's computer may or may not show the internet history of the sites viewed using the computer as a proxy. The first generation of anonymizer Trojan horses tended to leave their tracks in the page view histories of the host computer. Newer generations of the Trojan horse tend to "cover" their tracks more efficiently. Several versions of Sub7 have been widely circulated in the US and Europe and are the most widely distributed examples of this type of Trojan horse.
Current use
Due to the popularity of botnets among hackers and the availability of advertising services that permit authors to violate their users' privacy, Trojan horses are becoming more common. According to a survey conducted by BitDefender from January to June 2009, "Trojan-type malware is on the rise, accounting for 83-percent of the global malware detected in the world." This virus has a relationship with worms as it spreads with the help given by worms and travel across the internet with them.
Their main purpose is to make its host system open to access through the internet.
BitDefender also states that approximately 15% of computers are members of a botnet - usually an effect of a Trojan infection.
Common Trojan horses
- PC Optimiser pro (unknown creator)
- Netbus (by Carl-Fredrik Neikter)
- Subseven or Sub7(by Mobman)
- Back Orifice (Sir Dystic)
- Beast
- Zeus
- Trojan.Agent
- The Blackhole exploit kit
- Flashback Trojan (Trojan BackDoor.Flashback)
- ProRat
- ZeroAccess

